Deploy AI Agents, Cloud & QA Engineers in 3 Days - Cut Onsite Costs by 50%.
Facing delivery delays or hidden defects? Our AI-augmented platforms, Pitch N Hire and OnJob.io, match vetted AI engineers, cloud developers, and SDETs in 72 hours, accelerating releases and assuring zero-defect quality. Trusted by startups, enterprises, and AI innovators worldwide.
1,251+
Projects Delivered
72-Hours
Time to Deploy talent
60%
Cost Savings
Projects
The Tech That Powers Brands You Trust Daily!
Our Products
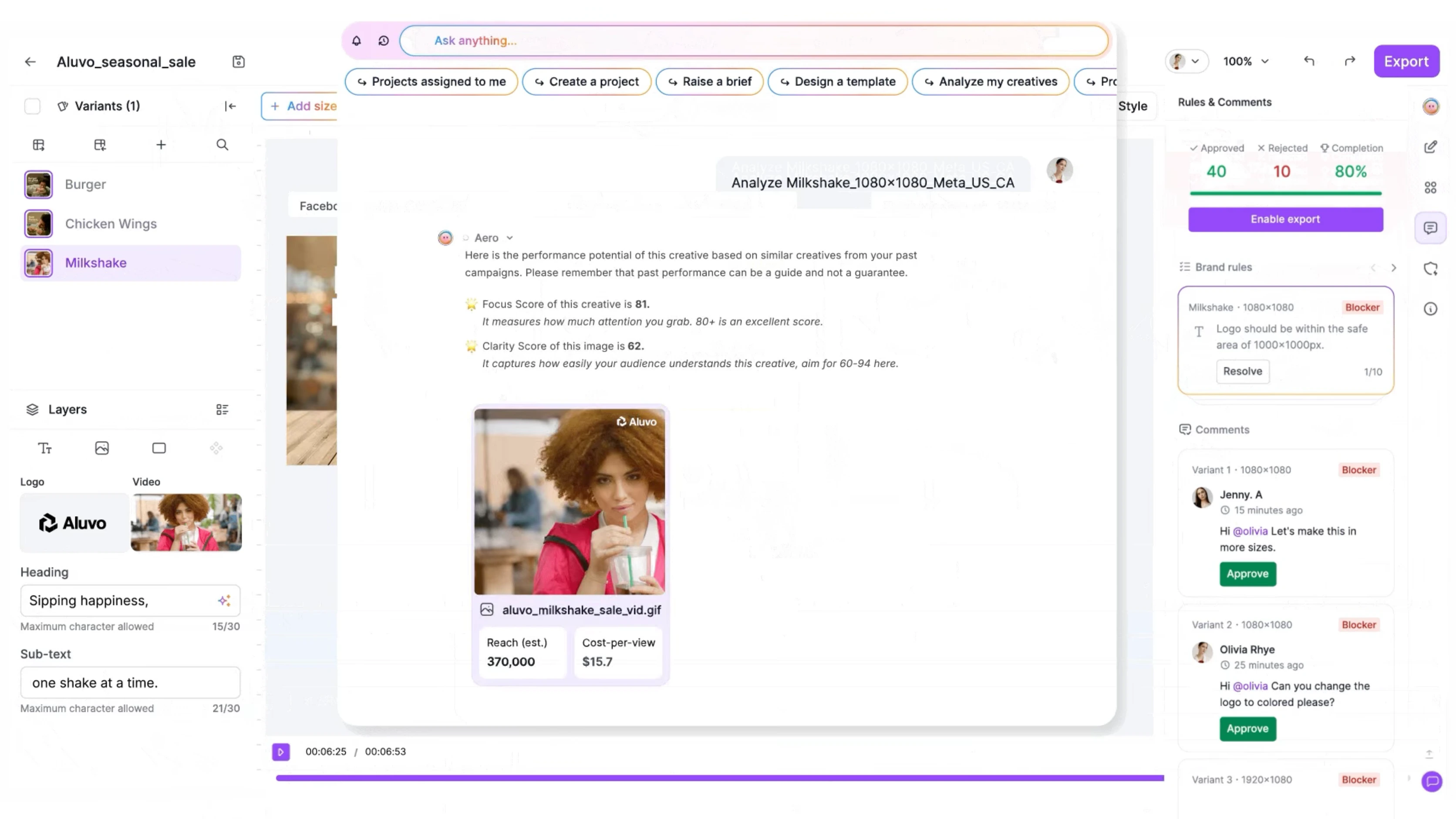
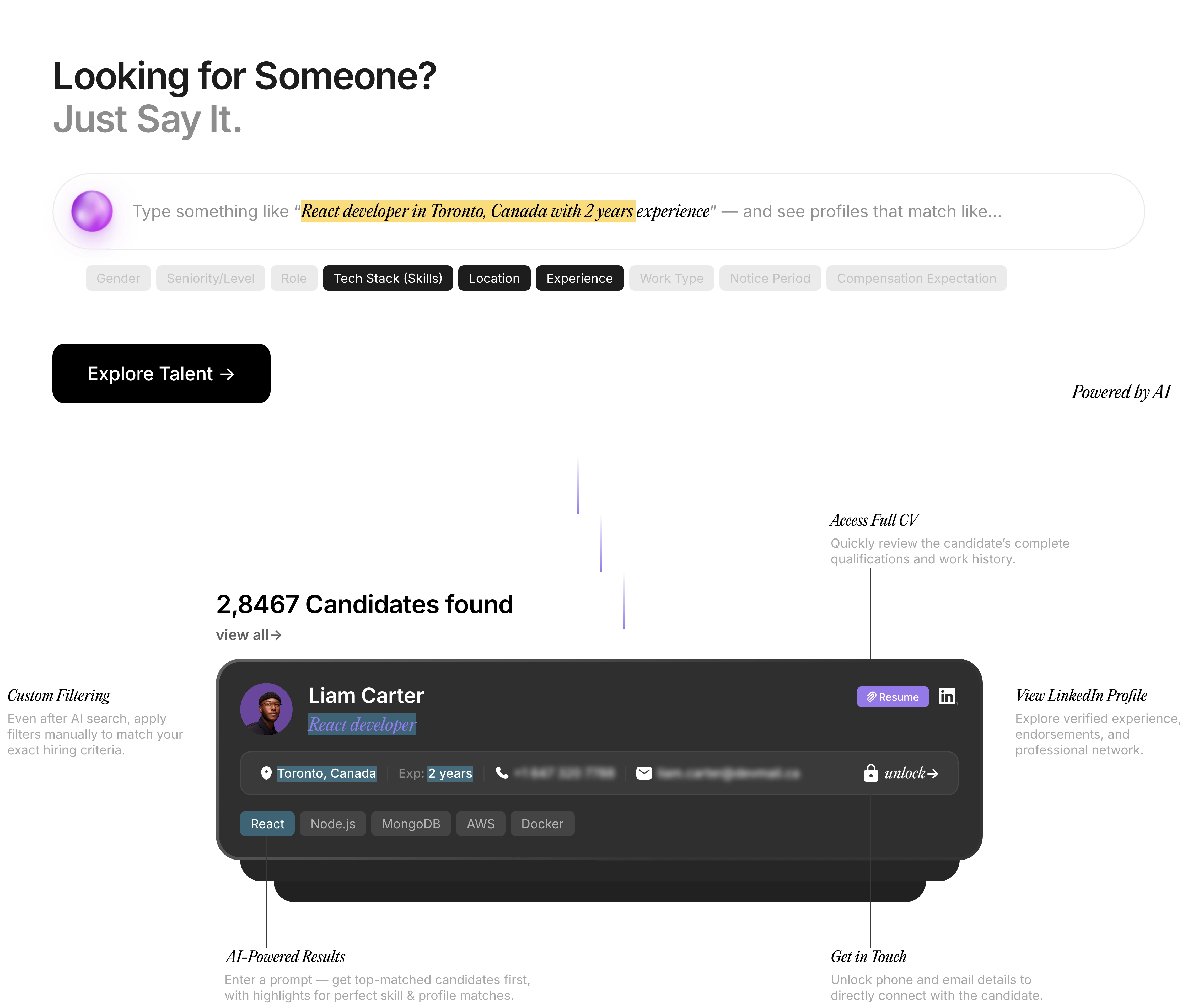
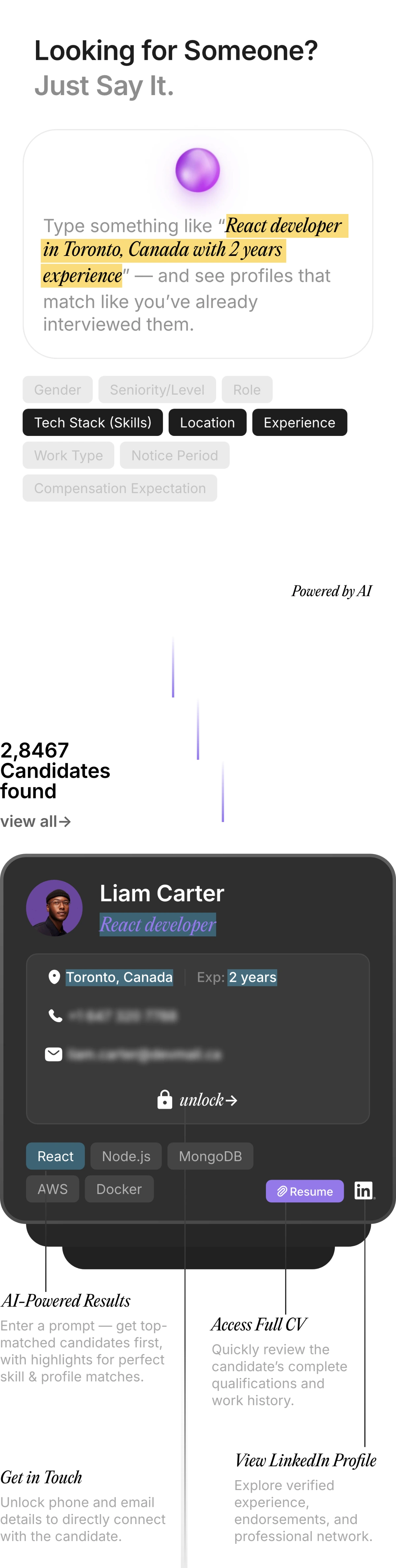
Rethinking Talent Acquisition with AI Led Hiring Platform !
Pitch N Hire and OnJob.io reimagine hiring—sourcing, scoring, and onboarding job-ready talent in days, not weeks. Deliver culturally aligned engineers with precision at scale, while automation removes repetitive screening so your team can focus on interviews, offers, and growth, with analytics.
Built for the AI Era. Engineered for Whats Next.
At Appsierra, we build outcomes—software that pays for itself, with intelligent systems learn, scale, and adapt.
From Fortune 500 to startup launches, our elite engineers, QA architects, and DevSecOps experts deliver precision at speed—modern stacks, automation, and measurable outcomes worldwide.
Whether it’s QA automation, AI hiring, or product engineering at scale, we help teams ship smarter and faster with accelerators, playbooks, and SLO-driven delivery globally.
AI-First Approach
Every workflow we build is tuned for intelligence, speed efficiency.
Global Engineering Talent
Vetted pods that scale with your roadmap
Zero-Defect Delivery
Shift-left testing + automation = flawless releases
Rapid Delivery Models
Get started in as little as 72 hours.
AI & ML Experts
Build copilots, predictive models, and automations with GenAI, NLP, LangChain, RAG, OpenAI, and Copilot to boost productivity and customer experience.
QA Automation & SDET
Ship with confidence using Selenium, Cypress, Playwright, and CI/CD integration now
Cloud & DevOps Professionals
Deploy on AWS, Azure, GCP, Kubernetes, and Terraform with DevSecOps expertise.
Blockchain Specialists
Build secure DApps, smart contracts, and auditable systems on Ethereum, Solidity, Hyperledger, and Chainlink for transparent, decentralized innovation
Edge AI & Embedded Systems
Power real-time IoT and 5G with Jetson, TensorRT, YOLOv8, and AWS IoT Core for reliable, connected devices.
Turn data into decisions with Tableau, Power BI, Python, and Looker—real-time dashboards and insights.
Data Analytics Leaders
Testimonials
What Our Clients Say About Scaling with AppSierra
4.8/5
Delivered 300+ success stories powering innovation for startups, enterprises, and SaaS leaders worldwide.







Trusted by 60+ global brands & growing.

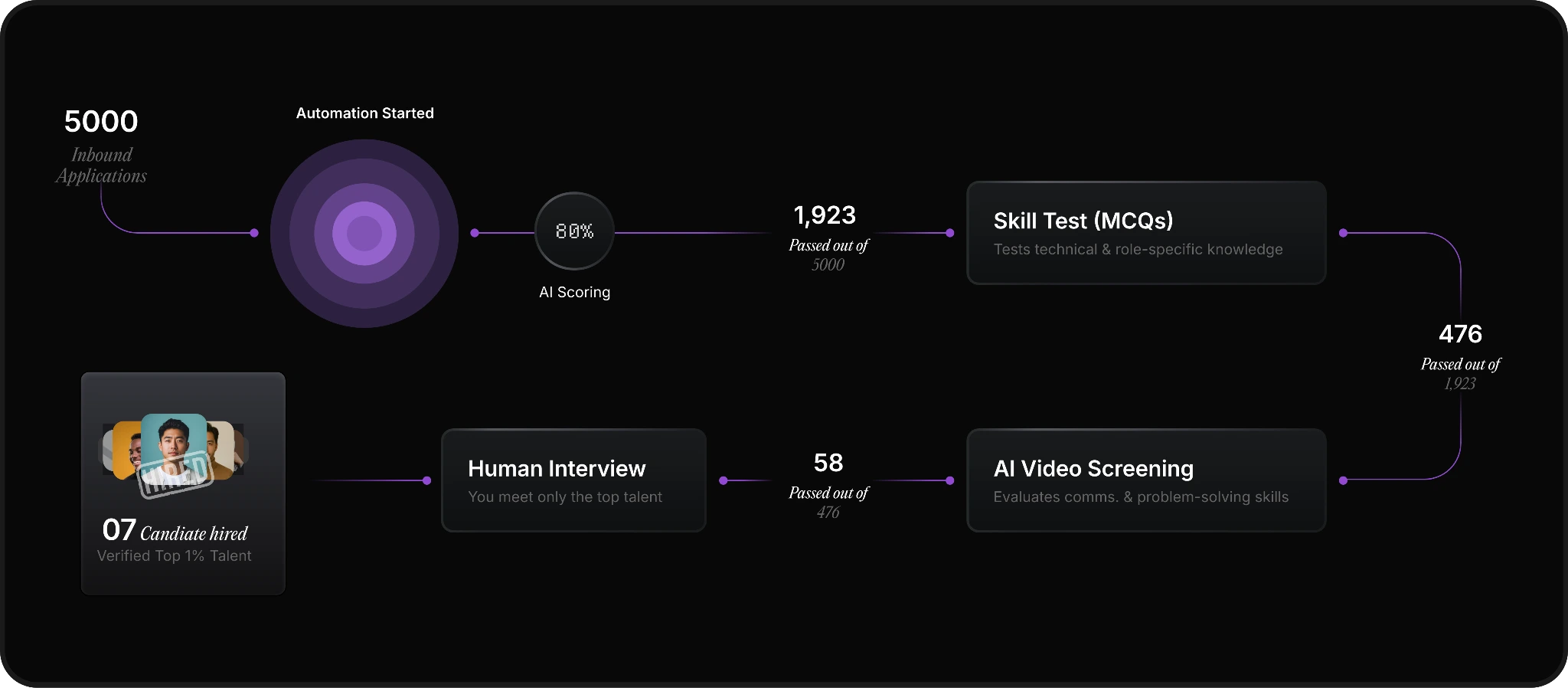
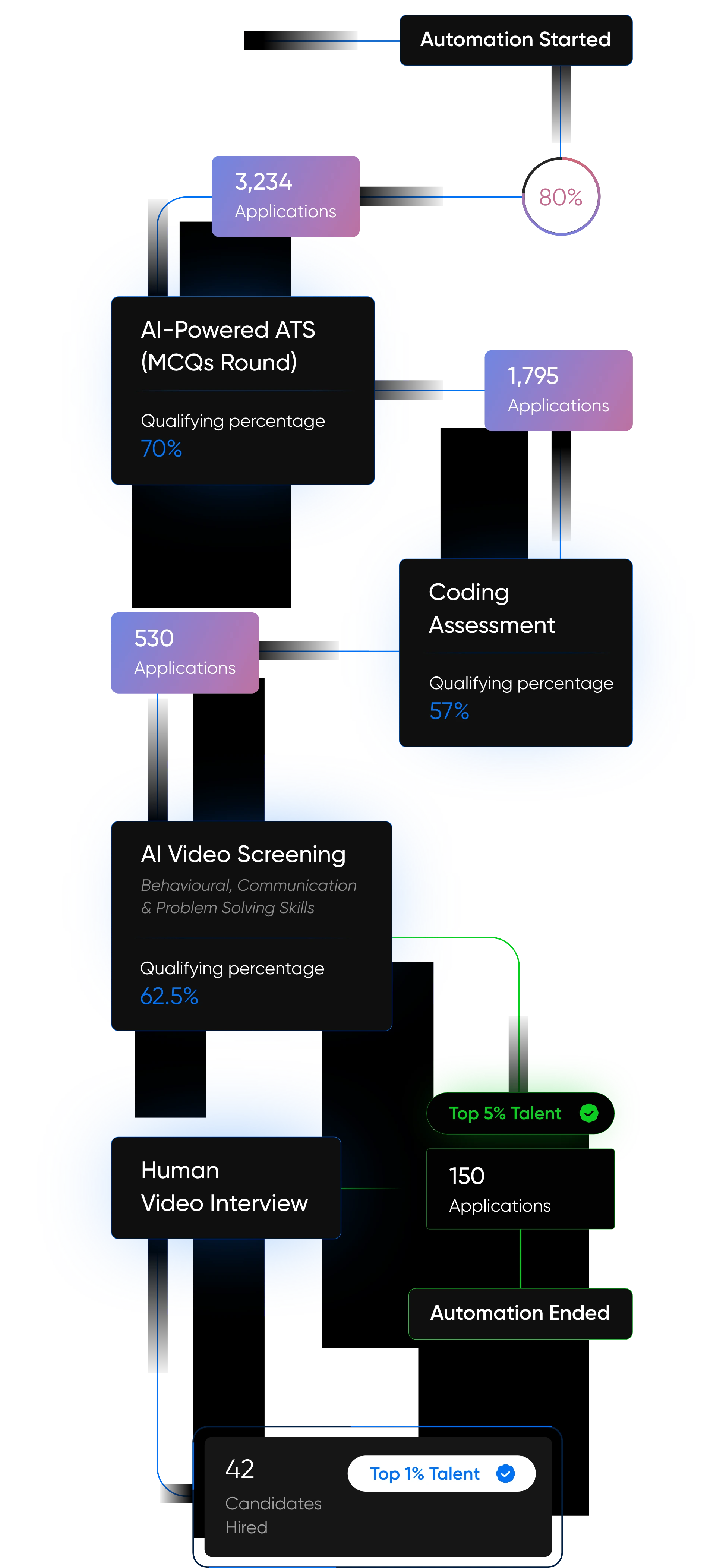
AI-Driven Hiring
Pitch N Hire and OnJob.io vet top 1% talent with scoring at 95% accuracy

End-to-End QA
Shift-left testing, automation, and DevSecOps zero-defect software.

Maximize ROI
Cut defects by 58% and hiring costs by 30% with precision and insights.

Scale with Confidence
Flex teams from 1 to 100+ engineers, aligned to roadmap and goals.

72-Hour Delivery
From request to deployment, faster than competitors 72 hours.
Enterprise-Grade Security
From DevSecOps to processes, we embed security into CI/CD, data, and code across the product lifecycle.
Success stories
Transformations That Speak for Themselves
Fintech Acceleration
With a leading fintech, we delivered a secure, scalable platform that streamlined operations, reduced fraud, and accelerated customer growth across channels, at speed and scale.
35%
Reduced transaction processing times significantly.
30%
Strengthened security protocols, lowering fraud incidents.
20%
Boosted customer acquisition through improved performance.
BFSI Excellence
With a major BFSI client, we implemented digital banking that reduced operational load, cut costs, and improved customer satisfaction with faster performance.
30%
Reduction in manual processes.
$8M
Annual savings in operational costs.
15%
Boosted customer acquisition through improved performance.
HealthTech Overhaul
We partnered with a healthcare leader to build a robust HIS—simplifying data access, lowering costs, and improving patient engagement with reliable secure workflows across clinics.
40%
Faster patient record access.
$6M
Annual cost reduction.
25%
Rise in patient satisfaction scores.