

The art of exploiting shortcomings and vulnerabilities in organizations, web applications, or individuals. This is not quite the same as playing out a weakness examination against your organization. Penetration testing takes the point of view of an external gatecrasher or an inward individual with a noxious purpose.
This may not generally include innovation; notwithstanding, specialized controls are a major piece of preventing simple misuse and information bargaining. It seems like each day brings another feature in regards to the most recent network safety threats.
Programmers keep on taking a huge number of records and billions of dollars at a disturbing frequency. To fight, they endeavour to conduct careful infiltration tests consistently. Penetration testing, also called pen testing, is intended to evaluate your security before an attacker does.

Pen testing devices reproduce certifiable attack situations to find and exploit security voids that could prompt records, traded off qualifications, licensed innovation, actually recognizable data, cardholder information, individual, ensured wellbeing data, information emancipate, or other destructive business results.
By misusing security weaknesses, entrance testing causes you to decide how to best relieve and shield your fundamental business information from future network safety attacks.
Even with the most grounded security and shields set up, weaknesses exist and expose an organization to obscure risks. Those voids may be just about as clueless as an information base, an application, or site access—even your representatives.
Also, any of those passages could give an immediate course into private electronic information, for example, financials, persistent data, or strategic documents. Pen testing services dive further to pinpoint pathways to get to, positioning the likely estimation of each and giving an unmistakable guide to remediation.
A penetration test isn’t just brilliant business practice; it is additionally a yearly prerequisite for individuals who should stay consistent with driving guidelines like PCI, HITECH, FISMA, SOX, FERPA, GLBA, FACTA, and GDPR.
A group of experienced, ethical hackers conducts an extensive appraisal of possible threats, focusing on those and prescribing approaches to hinder assaults before they harm any primary concern.
Looking for comprehensive SAP penetration testing services? Appsierra offers expert solutions to identify vulnerabilities and ensure the security of your SAP systems.
Pen testers aim to detect attacks done by persuaded hackers. To do so, they ordinarily follow an arrangement that incorporates the following steps:
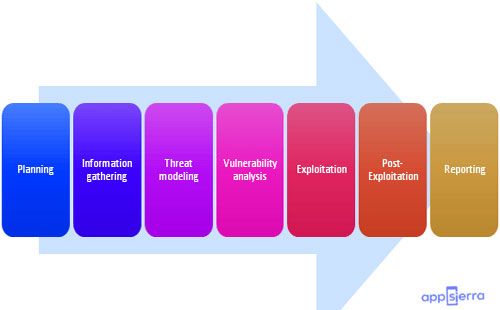
Assemble as much data about the objective as could be expected from public and private sources to illuminate the attack procedure. Sources incorporate web searches, space enlistment data recovery, social design, and non intrusive organization checking.
This data helps the pen testers map out the objective’s attack surface and potential weaknesses. Reconnaissance can shift with the degree and goals of the pen test and maybe just about as simple as settling on a telephone call to stroll through the usefulness of a framework.
The pen tester utilizes devices to inspect the objective site or framework for shortcomings, including open administrations, application security issues, and open-source weaknesses. Pen testers utilize an assortment of tools depending on what they find during reconnaissance and the test.
Attacker inspirations shift from taking, changing, or erasing information to moving assets to just harming your standing. To play out each experiment, pen testers should settle on the best instruments and methods to access your framework, regardless of whether through a shortcoming, like SQL injection or through malware or social design.
When pen testers access the objective, their stimulated assault should remain associated long enough to achieve their objectives: exfiltrating information, adjusting it, or mishandling functionality. It’s tied in with showing the possible effect.
The outcomes of the penetration test are then ordered into a report detailing:
This data is broken down by security faculty to help design an organization’s WAF settings and other application security solutions to fix weaknesses and ensure against future attacks.
Depending upon the objectives of a pen test, the association gives the testers shifting levels of data about, or admittance to, the objective framework. The penetration testing group sets a methodology toward the beginning and sticks with it.
On different occasions, the testing group advances their methodology as their attention to the framework increases during the pen test. In business, we talk around three sorts of pen tests:
The group has some information on at least one arrangement of qualifications. They additionally think about the objective’s inward information designs, code, and calculations. Pen testers may develop experiments dependent on point-by-point configuration records, like designs of the objective framework.
The group knows nothing about the inner design of the objective system. They go about as programmers would, examining for any remotely exploitable shortcomings.
For white box testing, pen testers approach frameworks and framework artefacts: source code, parallels, compartments, and, in some cases, even the workers running the framework. Get to know more about it on White Box Testing: Detailed Overview. White box approaches give the most significant level of confirmation at all measures of time.
There is no one answer for penetration testing. All things being equal, various targets require various arrangements of instruments for port examining, application filtering, Wi-Fi break-ins, or direct entrance of the organization. In any case, extensively speaking, the kinds of pen-testing tools fit into five classifications:

Below are the services of Penetration testing:
We assist organizations with relieving hazards because of inside dangers against their corporate organization. While external testing explores roads that far off programmers may use to enter networks, interior testing takes a look at ways representatives or insiders may prompt a break either through disregard, malice, or the coincidental download of an application, for example, ransomware or malware, which can cut a whole organization down.
The potential avenues of network attack are pinpointed where access may be acquired through web-associated servers or organization gear by people outside of your association who need fitting rights or certifications.
At that point, a mock attack is conducted to test security controls, creating and giving you a network safety appraisal on discoveries, alongside arrangements and proposals you can use to remediate the issue.
The possible dangers and weaknesses are researched and presented by the numerous web-based applications being used throughout your enterprise. Conveniently accessed from any area worldwide and simply penetrated, web applications offer critical purposes of access into Visa, client, and monetary information.
Vulnerability evaluation services explore the security of those arrangements and controls set up, giving proposals and methodologies to obstruct admittance to any information that may be put away inside.
We overview employees to perceive how well they comprehend an association’s data security arrangements and practices so that one can realize how effectively an unapproved gathering may persuade staff into sharing secret data.
This testing may incorporate identification passageways, false phishing assaults or secret phrase update demands. At that point, a prescribed approach is recommended to improve accomplishment through preparing or new cycles that help representatives better secure touchy information.
A progressing ability in the scope of remote advances is brought, offering moral hacking administrations to explore and recognize potential passages where programmers could enter the inward organization.
This includes danger evaluation and security control reviews for customary Wi-Fi and specific frameworks. The discoveries are assembled into an online protection appraisal report with suggestions you can establish to moderate harm.
Through penetration testing, security experts can adequately discover and test the security of multi-level organization models, custom applications, web administrations, and other IT segments. These penetration testing devices and administrations help you acquire quick knowledge into the zones of most elevated danger with the goal that you may adequately design security financial plans and undertakings.
Completely testing the aggregate of a business’ IT framework is basic to playing it safe and expected to get indispensable information from network protection programmers, while at the same time improving the reaction season of an IT department in case of an attack.